I add mime maps manually to IIS manager and also add them to webconfig file. I'm getting this error. To add a MIME type for a virtual directory within a website: Go to Websites & Domains and find the website’s domain name. Click Virtual Directories. Navigate to the required virtual directory and click the corresponding link with its name. Click the MIME Types tab. Click Add MIME Type. Specify the following: Type the file name extension in.
Добавил:Webhint, a linting tool for the web focused on best practices and flexibility for the end user. (IIS 7.0) Set MIME types. FH Web uses.xpi and.dmg extensions for client computers that use Safari or Firefox as a browser. For these plug-ins to run, IIS 7.0 requires that you have a document with an extension that does not have a registered MIME type on that server.
Вуз:Предмет:Файл:Скачиваний:Добавлен: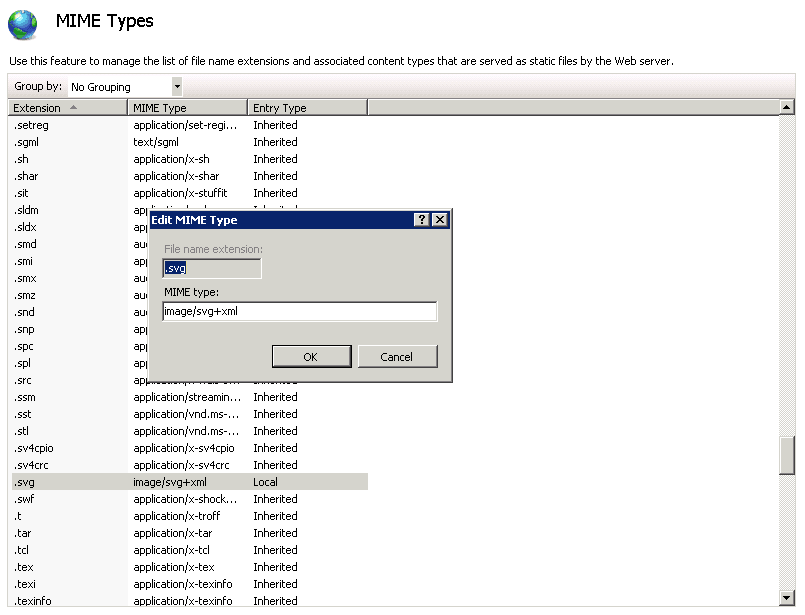
Chapter 1
IIS Request Handling
The initial processing of an HTTP request on Windows Server 2003 occurs within both IIS and a supporting protocol driver. As a result, depending on the configuration for IIS, a request may never make it far enough to be processed by ASP.NET. The diagram in Figure 1-1 shows the salient portions of IIS and Windows Server 2003 that participate in request processing.
Worker process | ||
w3wp.exe | ||
static content | aspnet_isapi.dll | asp.dll |
aspnet_filter.dll | ||
ISAPI filters | ||
Request for | http.sys | |
default.aspx | ||
Figure 1-1 |
A request must first make it past the restrictions enforced by the kernel mode HTTP driver: http.sys. The request is handed off to a worker process where it then flows through a combination of the internal request processing provided by IIS and several ISAPI filters and extensions. Ultimately, the request is routed to the appropriate content handler, which for ASP.NET pages is the ASP.NET runtime’s ISAPI extension.
Initial Phases of a Web Request
Http.sys
When an HTTP request is first received by Windows Server 2003, the initial handling is actually performed by the kernel-mode HTTP driver: http.sys. The kernel mode driver has several Registry switches that control the amount of information allowed in a request URL. By default the combined size of the request URL and associated headers — any query string information on the URL, and individual headers sent along with the request, such as cookie headers — must not exceed 16KB.
Furthermore, no individual header may exceed 16KB. So, for example, a user agent could not attempt to send a cookie that is larger than 16KB (although for other reasons, a 16KB cookie would be rejected by ASP.NET anyway). Under normal circumstances the restrictions on headers and on the total combined size of the request URL and headers is not a problem for ASP.NET applications. However, if your application depends on placing large amounts of information in the URL — perhaps for HTTP-based .asmx Web Services — then the length limit enforced by http.sys may come into play.
Any application that depends on excessively long request URLs or request headers should, if at all possible, have its logic changed to transmit the information through other mechanisms. For a Web Service, this means using Simple Object Access Protocol (SOAP) headers to encapsulate additional request data. For a website, information needs to be sent using a POST verb, rather than a GET verb.
The kernel mode driver restricts the number of path segments in a URL and the maximum length for any individual path segment. Examine the following URL:
http://yoursite/application1/subdirectory2/resource.aspx
The values application1, subdirectory2, and resource.aspx represent individual path segments. By default, http.sys disallows URLs that have more than 255 path segments and URLs where the length of any single path segment exceeds 260 characters. These constraints are actually pretty generous, because in practice developers normally do not need large number of path segments, even for applications with a fair amount of directory nesting. The requested page in the previous example, resource.aspx, is considered a path segment and is subject to the same length restrictions as any portion of the URL. However, if there were query string variables after resource.aspx, the length of the query string variables would apply only against the overall 16KB size restriction on the combined size of URL plus headers. As a result, you can have query string variables with values that are greater than 260 characters in length.
One reason for these size limits is that a number of hack attacks against web servers involve encoding the URL with different character representations. For example, an attacker may attempt to bypass directory traversal restrictions by encoding periods like this:
http://yoursite/somevirtualdirectory/%2E%2E/%2E%2E/%2E%2E/boot.ini
As you can see, encoding characters bloats the size of the URL, so it is reasonable to assume that excessively long URLs are likely due to hacker attempts.
To give you a concrete example of http.sys blocking a URL, consider a request of the following form:
http://localhost/123456789012345678901234567890etc.../foo.htm
The sequence 1234567890 is repeated 26 times in the URL. Because the path segment is exactly 260 characters though, http.sys does not reject the request. Instead, this URL results in a 404 from IIS because there is no foo.htm file on the system.
However, if you add one more character to this sequence, thus making the path segment 261 characters long, an HTTP 400 - Bad Request error message is returned. In this case, the request never makes it far enough for IIS to attempt to find a file called foo.htm. Instead, http.sys rejects the URL and additional IIS processing never occurs. This type of URL restriction reduces the load on IIS6, because IIS6 does not have to waste processor cycles attempting to parse and process a bogus URL.
This raises the question of how a web server administrator can track URL requests are being rejected. The http.sys driver will log all errors (not just security-related errors) to a special HTTP error log file. On Windows Server 2003, inside of the %windir%system32LogFiles directory, there is an HTTPERR subdirectory. Inside of the directory one or more log files contain errors that were trapped by http.sys. In the case of the rejected URLs, a log entry looks like:
2005-03-13 22:09:50 127.0.0.1 1302 127.0.0.1 80 HTTP/1.1 GET /1234567890 | ....htm 400 |
- URL |
For brevity the remainder of the GET URL has been snipped in the previous example; however, the log file will contain the first 4096 bytes of the requested URL. In this example, the value URL at the end of the log entry indicates that parsing of the URL failed because one of the path segment restrictions was exceeded.
If the URL is larger than 16KB, the log entry ends with URL_Length, indicating that the allowable URL length had been exceeded. An example of such a log entry is:
2005-03-13 23:02:53 127.0.0.1 1086 127.0.0.1 80 HTTP/0.0 GET - 414 -
URL_Length
For brevity, the URL that caused this is not included because a 16KB long URL would not be particularly interesting to slog through. Remember that form posts and file uploads also include a message body that usually contains the vast majority of the content being sent to the web server. Because http.sys only checks the URL and associated headers, it does not perform any validation on the size of the message body. Instead it is ASP.NET that is responsible for limiting the size of raw form post data or file uploads.

A subtle point about the previous discussion is that some of the restrictions http.sys enforces are based on number of characters, while other restrictions are based on byte size. In the case of path segments, the restrictions are based on number of characters, regardless of the underlying character set. However, for the 16KB size restrictions, the actual URL or header allowed depends heavily on the characters in the URL or headers. If a URL or header contains only standard ASCII characters, a 16KB size limit equates to 16384 characters. However, if a URL or header contains characters other than standard ASCII characters, converting from byte size to character length becomes a bit murkier.
Because http.sys processes URLs as UTF-8 by default, and UTF-8 characters consume between 1 and 3 bytes in memory, an allowable URL length could be anywhere from roughly 5461 characters to 16384 characters. A general rule of thumb when using non-ASCII characters though is to assume 2 bytes per character if there is extensive use of Unicode characters, which equates to a maximum URL length (including query string variables) of 8192 characters.
Initial Phases of a Web Request
The character length and byte size restrictions enforced by http.sys can be modified by adding DWORD values underneath the following Registry key:
HKEY_LOCAL_MACHINESystemCurrentControlSetServicesHTTPParameters
The specific Registry settings that govern the behavior just discussed are listed in the following table. Also, a server reboot is required after you change any of the following settings.
Registry Setting Value Name | Description |
MaxFieldLength | By default, an individual header can be up to 16KB in size. |
Change this setting to limit the size of any individual HTTP | |
header. A request URL, including query string information, is | |
also restricted in size by this setting. The allowed range of | |
values is 64–65534 bytes. | |
MaxRequestBytes | By default, the combined size of the request URL, including |
query string, plus its associated HTTP headers cannot exceed | |
16KB. The allowed range of values is 256–16777216 bytes. | |
UrlSegmentMaxCount | By default, no more than 255 path segments are allowed in a |
URL. The allowed range of values is 0–16383 segments. | |
UrlSegmentMaxLength | By default, an individual path segment cannot be longer than |
260 characters. The slashes that delimit each path segment | |
are not included when computing a path segment’s character | |
length. The allowed range of values is 0–32766 characters. |
In earlier versions of IIS, the URLScan security tool (available by searching microsoft.com/technet) provides similar protections for restricting URLs. Most of the security functionality of URLScan was incorporated into http.sys and IIS6. There are a few small features that are only available with URLScan though, the most interesting one being URLScan’s ability to remove the server identification header that IIS sends back in HTTP responses.
aspnet_filter.dll
After http.sys is satisfied that the request is potentially valid, it passes the request to the appropriate worker process. In IIS6 multiple application pools can be running simultaneously, with each application essentially acting as a self-contained world running inside of an executable (w3wp.exe). Within each worker process, IIS carries out a number of processing steps based on the ISAPI extensibility mechanism. Even though ASP.NET is a managed code execution environment, it still depends on the ISAPI mechanism for some initial processing.
When ASP.NET is installed on a web server, it registers an ISAPI filter with IIS. This filter (aspnet_ filter.dll) is responsible for two primary tasks:
Managing cookieless tickets by converting them into HTTP headers
Preventing access over the Web to protected ASP.NET directories
Chapter 1
You can see the set of all ISAPI filters that are registered in IIS by using the IIS MMC, right-clicking the Web Sites node, and then clicking on the ISAPI Filters tab in the dialog box that opens. In Figure 1-2, you can see that there is currently only one ISAPI filter registered by default — the ASP.NET filter. Depending on your machine, you may see additional filters that provide services such as compression or that support Front Page extensions.
Figure 1-2
By default ASP.NET registers the filter with a Low priority, which means that other filters with higher priorities will have the opportunity to inspect and potentially modify each incoming request. This makes sense because if, for example, you are running a filter that decompresses incoming HTTP content, you would want this type of operation to occur prior to ASP.NET carrying out security logic based on the request’s contents.
The ASP.NET filter handles two ISAPI filter notifications: SF_NOTIFY_PREPROC_HEADERS and SF_NOTIFY_URL_MAP. This means the filter has the opportunity to manipulate the request prior to IIS attempting to do anything with the HTTP headers, and the filter has the opportunity to perform some extra processing while IIS is converting the incoming HTTP request into a request for a resource located at a specific physical path on disk.
Processing Headers
The ASP.NET filter inspects the request URL, looking for any cookieless tickets. In ASP.NET 2.0, cookieless tickets are supported for session state (this was also available in 1.1), forms authentication (previously available as part of the mobile support in ASP.NET) and anonymous identification (new in ASP.NET 2.0). A sample URL with a cookieless session state ticket is shown here:
http://localhost/inproc/(S(tuucni55xfzj2xqx1mnqdg55))/Default.aspx
Initial Phases of a Web Request
ASP.NET reserves the path segment immediately after the application’s virtual root as the location on the URL where cookieless tickets are stored. In this example, the application was called inproc, so the next path segment is where ASP.NET stored the cookieless tickets. All cookieless tickets are stored within an outer pair of parentheses. Within these, there can be a number of cookieless tickets, each starting with a single letter indicating the feature that consumes the ticket, followed by a pair of parentheses that contain the cookieless ticket. Currently, the following three identifiers are used:
S — Cookieless ticket for session state
A — Cookieless ticket for anonymous identification
F — Cookieless ticket for forms authentication
However, the ASP.NET filter does not actually understand any of these three indentifiers. Instead, the filter searches for the character sequences described earlier. Each time it finds such a character sequence, it removes the cookieless ticket, the feature identifier and the containing parentheses from the URL and internally builds up a string that represents the set of cookieless tickets that it found. The end result is that all cookieless tickets are removed from the URL before IIS attempts to convert the URL into a physical path on disk. Therefore, IIS doesn’t return a 404 error even though there clearly is no directory on disk that starts with (S).
After the filter removes the tickets from the URL, it still needs some way to pass the information on to the ASP.NET runtime. This is accomplished by setting a custom HTTP header called ASPFILTERSESSIONID. The name is somewhat misleading because it is a holdover from ASP.NET 1.1 when the only cookieless ticket that was supported (excluding mobile controls and the cookieless forms authentication support that was part of the mobile controls) was for session state. With ASP.NET 2.0, though, there are obviously a few more cookieless features integrated into the product. Because the underlying logic already existed in the ISAPI filter, the old header name was simply retained.
You can actually see the effect of this header manipulation if you dump the raw server variables associated with an ASP.NET request. As an example, for an application that uses both cookieless session state and cookieless forms authentication, the URL after login may look as follows:
http://localhost/inproc/(S(sfeisy55occclkmlkcwtjz55)F(jbZ....guo1))/Default.aspx
For brevity the majority of the forms authentication ticket has been removed. However, the example shows cookieless tickets for session state and forms authentication in the URL. If you were to dump out the server variables on a page, you would see the following header:
HTTP_ASPFILTERSESSIONID=S(sfeisy55occclkmlkcwtjz55)F(jbZ....guo1)
Hopefully, this sample makes it clearer how the unmanaged ISAPI ASP.NET filter transfers cookieless tickets over to the ASP.NET runtime. Within the ASP.NET runtime, the HTTP modules that depend on these tickets have special logic that explicitly looks for this HTTP header and parses out the ticket information for further processing (for example, setting up the session, validating forms authentication credentials, and so on).
Chapter 1
Blocking Restricted Directories
After the filter processes any cookieless tickets, the filter has IIS normalize the request URL’s representation. This is necessary because the filter enforces the restriction that browser users cannot request any type of content from the protected directories in ASP.NET 2.0. Because ASP.NET 2.0 introduced new “content” that in reality consists of code, data, resources, and other pieces of information, it is necessary to prevent access to this information via a browser. The filter prevents access by scanning the normalized URL, looking for one of the following paths:
/bin — Compiled assemblies referenced by the application
/app_code — Source code files with classes referenced elsewhere in an application
/app_data — Data files such as .xml, .mdb, or .mdf files
/app_globalresources — Resources that are globally accessible throughout an application
/app_localresources — Resources that are applicable to a specific directory
/app_webreferences — WSDL files and compiled artifacts for Web Services
/app_browsers — Browser capability files for determining browser functionality
If the filter finds a path segment with one of these paths, the filter returns an error to IIS, which is converted into a 404 response and returned to the browser. For example, if a web server has a directory immediately under wwwroot called app_data with an HTML file called foo.htm, requesting the following URL still result in a 404 even though the file does exist on the file system.
http://localhost/app_data/foo.htm
There had been some discussion at one point around having the filter perform a broad blocking of any URLs that contained the characters /app_ at the beginning of a path segment. However, this decision was avoided because some developers may have already been using such a naming prefix in their directory structures. If at all possible, it is recommended that developers move away from naming any directories with the /app_ prefix. In a future release of ASP.NET, the filter may support blocking any paths that
start with these characters — not just the specific set of reserved directories in ASP.NET 2.0.
If you have valid reasons for creating directory structures on disk with any of the reserved names noted earlier, you can disable the filter’s directory blocking behavior (although for security reasons this is clearly not recommended). Registry settings to control the directory blocking behavior can be added as DWORD values underneath the following Registry key:
HKEY_LOCAL_MACHINESoftwareMicrosoftASP.NET
After changing any of the settings shown in the following table, run iisreset to recycle the worker processes. This forces aspnet_filter.dll to read the new Registry settings when the filter is initialized in a new worker process.
Initial Phases of a Web Request | |
Registry Setting Value Name | Description |
StopBinFiltering | Set this value to 1 to stop the filter from blocking |
requests to paths that include /bin. This setting | |
will affect all ASP.NET 1.1 and 2.0 applications on | |
the server. | |
StopProtectedDirectoryFiltering | Set this value to 1 to stop the filter from blocking |
requests to reserved ASP.NET directories that | |
include a path starting with /app_. Because this | |
setting is new to ASP.NET 2.0, it will only affect all | |
ASP.NET 2.0 applications on the server. |
Setting either one of these Registry settings will affect all of your websites. There is no mechanism to selectively turn off directory blocking for only specific applications or specific websites.
Dynamic versus Static Content
After a request has flowed through all of the ISAPI filters configured for a website, IIS decides whether the requested resource is considered static content or dynamic content. This decision really depends on whether a custom ISAPI extension has been configured and associated with the file extension of the requested resource. For example, if you were to request http://localhost/foo.htm, in the default configuration of IIS, the .htm extension is registered as a type of static content server directly by IIS.
The configuration of static versus dynamic content is determined by a combination of settings in IIS6:
MIME type mappings
File extension to ISAPI extension mappings
The presence of wildcard application mappings (if any)
MIME Type Mappings
IIS6 is configured with several well known static file extensions in its list of Multipurpose Internet Mail Extensions (MIME) type mappings. The reason that MIME type mappings are so important in IIS6 is that without a MIME type mapping, an HTTP request for a file results in a 404 error, even if the file does exist on the file system. For example, if a text file, foo.xyz, exists at the root of a website, requesting http://localhost/foo.xyz results in a 404.
However, the web server’s allowable MIME types can be edited to allow IIS6 to recognize .xyz as a valid file extension. In Figure 1-3, the IIS6 MMC is shown being used to register .xyz as a valid file extension.
Chapter 1
Figure 1- 3
Right clicking the computer node and selecting Properties pulls up a dialog box that allows you to configure MIME types. Click the MIME Types button to access the Mime Types dialog box, where you can click the New button to add a new MIME type. For this example, the .xyz file extension was added as a being a text type.
You need to iisreset for the changes to take affect. When the web server is running again, a request for http://localhost/foo.xyz works, and IIS6 returns the file’s contents.
ISAPI Extension Mappings
Because a web server that serves only static files would be pretty useless in today’s web, ISAPI extension mappings are available for serving dynamically generated content. However, ISAPI extensions can also be used to carry out server-side processing on static file content. For example, there are ISAPI extensions for processing server-side include files. In practice though, ISAPI extensions are typically used for associating file extensions with Dynamic Link Libraries (DLLs) that carry out the necessary logic for executing code and script to dynamically generate page output.
Initial Phases of a Web Request
You can see the list of ISAPI extensions that are mapped to a website with the following steps:
1.Right-click the application’s icon in the IIS6 MMC.
2.Select properties.
3.In the Directory tab of the dialog box that pops up, click the Configuration button.
4.In the Mappings tab of the dialog box that pops up, a list box shows all application extensions currently mapped for the web application.
Iso Mime Type Iis
In Figure 1-4, the current application has mapped the .aspx file extension to a rather lengthy path that lives somewhere in the framework installation directory.
Figure 1-4
Iis Mime Type List
The path is too long to see without scrolling around, but it points at the following directory location:
%windir%Microsoft.NETFrameworkv2.0.50727aspnet_isapi.dll
Depending on where you installed the operating system on your machine, the location of %windir% will vary.
Тут вы можете оставить комментарий к выбранному абзацу или сообщить об ошибке.
Оставленные комментарии видны всем.
Add Dmg To Iis Mime Type 2
Соседние файлы в предмете ПрограммированиеAspx Mime Type Iis
- #17.08.201315.94 Mб29Ajax Patterns And Best Practices (2006).pdf
- #17.08.201316.82 Кб18Alternate Data Streams in NTFS.pdf
- #17.08.201316.43 Кб24An Example of the RSA Algorithm.pdf
- #17.08.201329.59 Кб14Analysis of a Telnet Session Hijack via Spoofed MAC Addresses.pdf
- #17.08.201312.33 Mб44Asp Net 2.0 Security Membership And Role Management.pdf
- #17.08.20137.66 Mб55ASP Programming for the Absolute Beginner.pdf
- #17.08.201310.07 Mб50ASP.NET 2.0 Everyday Apps For Dummies (2006).pdf
- #17.08.201310.27 Mб38ASP.NET 2.0 Everyday Apps for Dummies.pdf
- #17.08.201311.03 Mб55ASP.NET 2.0 Instant Results.pdf
- #17.08.201313.24 Mб25ASP.NET 2.0 Visual Web Developer 2005 Express Edition Starter Kit (2006).pdf